ConnectWise ScreenConnect Attack
Overview
An IT remote access tool actively targeted
Threat actors including ransomware gangs are seen exploiting newly discovered critical flaws in remote monitoring and management software called ScreenConnect. Learn More »
Common Vulnerabilities and Exposures
Background
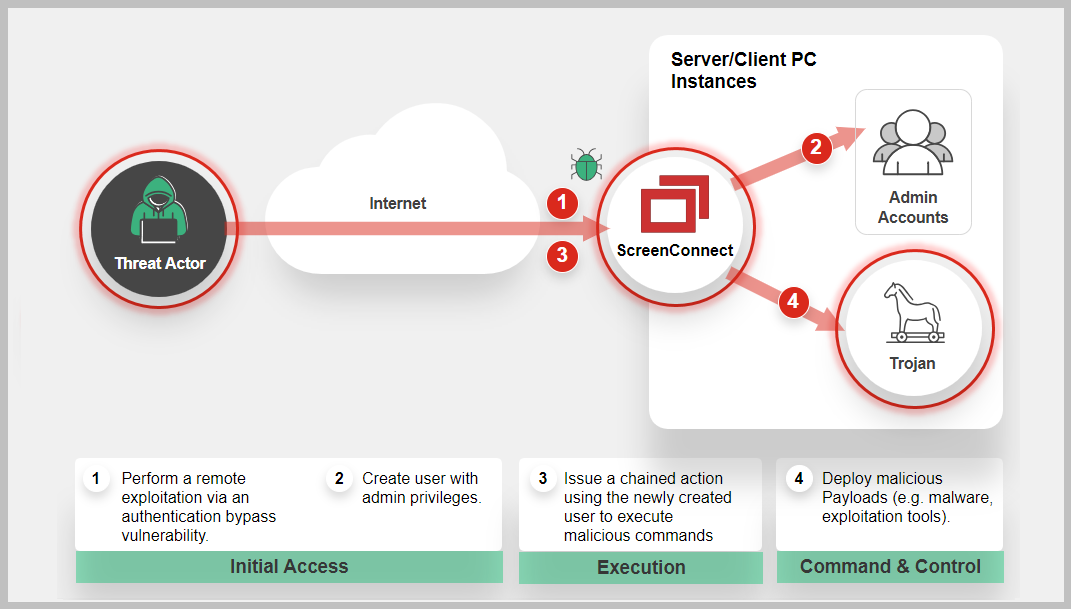
One of the flaws, CVE-2024-1709 is an authentication bypass vulnerability using an alternate path or channel that could let attackers gain administrative access to a ScreenConnect instance. The second flaw tracked as CVE-2024-1708 is a path traversal vulnerability that may allow an attacker to execute remote code. According to Shadowserver, around 8200 vulnerable ConnectWise ScreenConnect instances were found on the internet and 643 IPs were observed attacking it. According to the company website, ConnectWise remote-access software is one of the leading providers used by Managed service providers (MSPs) to remotely connect to their customer's systems. This could pose a significant threat to end user's systems that could be targeted downstream and can allow hackers to plant malicious code remotely.
Analysis
Latest Development
February 19, 2024: ConnectWise published a security advisory and has released a patch covering both vulnerabilities.https://www.connectwise.com/company/trust/security-bulletins/connectwise-screenconnect-23.9.8
February 21, 2024: Proof of Concept (PoC) code was released on GitHub. February 22, 2024: CVE-2024-1709 was added to CISA's known exploited catalog.https://www.cisa.gov/known-exploited-vulnerabilities-catalogFebruary 22, 2024: FortiGuard Labs released a Threat Signal on ConnectWise ScreenConnect Vulnerabilities (CVE-2024-1708 and CVE-2024-1709)https://www.fortiguard.com/threat-signal-report/5389/
FortiGuard Labs recommends companies to apply the most recent upgrade or patch from the vendor as soon as possible.
Solutions
FortiGuard Cybersecurity Framework
Mitigate security threats and vulnerabilities by leveraging the range of FortiGuard Services.
Protect :
- AV
- Vulnerability
- AV(Pre-filter)
- IPS
Detect :
- Outbreak Detection
- Threat Hunting
Respond :
- Assisted Response Service
- Automated Response
Recover :
- NOS/SOC Training
- End-User Training
Identify :
- Vulnerability Management
- Attack Surface Hardening
- Busines Reputation